Segregation of Duties on a globalized culture?
Segregation word might be understand as a negative word. When administering IT systems, we DO have to segregate everything… segregate, divide, categorize, organize and so on. So segregation of Duties is a good IT topic.
As Occam’s Razors says, “the simplest solution is almost always the best.”, and this is true meanwhile we commit all our policies and best practices. For sure, having a single identity (say user ID on Active Directory) is the simplest implementation, but does not follows many security policies and market standard best practices.
If we have a single identity (let’s say Hans Solo or soloh, just as an example) which he uses to read email, but not only corporate, personal as well, for web surfing, to print those nice presentations… and additionally to administer one or several servers… to manage a web server… to create users and groups… …and so on is not what our IT environment needs. Now you might be getting some clarity: this simple model cannot guarantee the security of all the environments soloh manages.
Neuron fight result… an idea
So yes, we must segregate. Mainly we must segregate rights and permissions, and most likely on the several environments present in our network. We cannot afford the risk of exposing credentials, and worst if those credentials have some sort of rights or privileges. If we keep separated our food from soaps and cleaners (imagine a pancake of dishwasher with syrup of vanilla hands soap!), then why we should maintain the same multi-purpose account; is difficult to know what this account can accomplish, where it can do it, and if this action is legitimate.
Solution is quite simple. Create a new, exclusive account for any administration purpose. I have to admit that having more than 1 identity (or userID in AD world) is not simpler, nevertheless having into consideration that I must maintain separation because of the usage of each identity, then yes, is the simplest approach while maintaining my security.
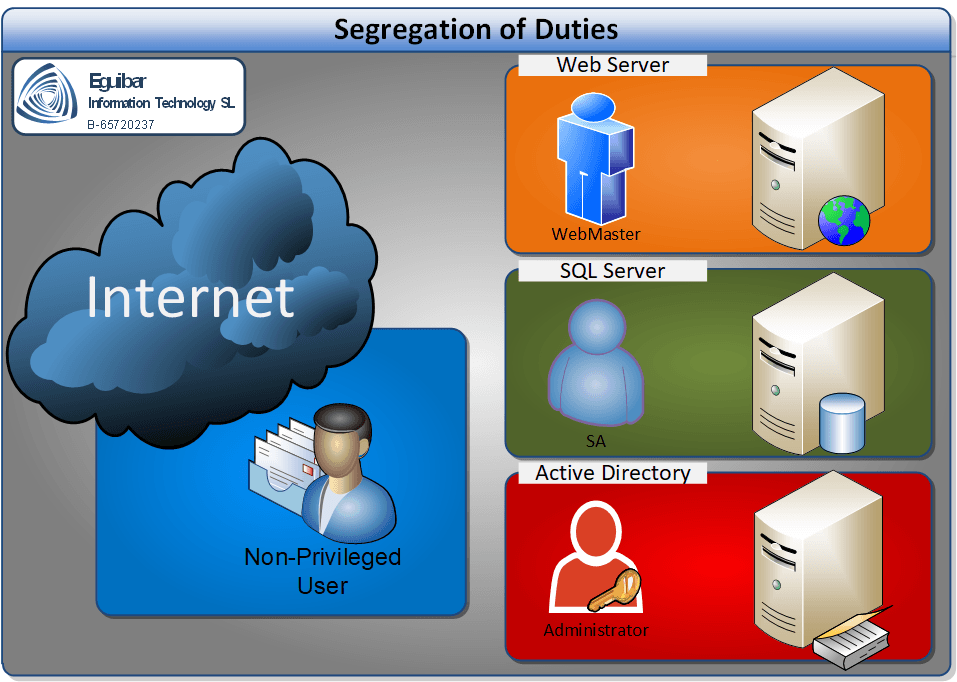
Now that there is no doubt on why I must segregate, it comes the next question: what needs segregation? Again, a puzzling question to answer; a deeper analysis of your daily operations has to be done in order to identify assets, more important critical assets… but as a rule of thumb, keep a standard user away form IT Administrative tasks. Now we end up having 2 categories: Non-Privileged Users (or standard users) and Administrative users.
In the event (an unpleasant event we don’t wanna see!) that our Non-Privileged user soloh gets compromised, the damage remains, just because this standard user has limited permissions. On the other hand, what will happen if the Administrative account soloh-Admin is at risk… well, then we have to worry, and start to run. Furthermore, we will consider new segregation for administrative proposes. Imagine that our user soloh has to administer some shares on file servers, the HHRR database, and our mighty Active Directory, then we will create one admin account for each of the roles: soloh_Share, soloh_SQL and soloh_AD.
How much is a little?
Ok, but how much is enough? Several factors to consider before giving an educated response:
- How much money and/or business will you lose in case of a breach?
- How much time will you be unable to work until coming back to normal operation?
- How much damaged will end up your enterprise image after the event?
The answer is yes, it has to be enough; let me bring an example… you decide to change the local Admin password every month in your 500 computers and servers, however this password is the same for all. Then as soon as 1 computer is in compromise, the 499 remaining computers are in compromise as well. As an alternative, you can have a different password to each of them; so in the event that one gets compromised, the remaining 499 are partially safe. This is Segregation of Assets.
What would I do if I’m working for you
Starting from the beginning, separate a normal or Non-Privileged user from an Administrator or Privileged User. Normal user becomes exposed on unsecure networks like the Internet or by malicious emails. Any Privileged user should avoid such insecurity. An effortless way forward to security is to provision new identities for administration purposes.
Once we segregate the non-privileged users, we must have a clear understanding on daily operations. What are Admins doing and how are they doing it. Having this information, we can start creating several administration areas, each one of them having its own privileged users segregated from other areas.
And last, but not least, make a magic trick: make disappear ALL shared accounts. If you cannot make them disappear (as in the case of Built-In Administrator accounts), then change its password to something ridiculous long, and keep it away from Admin users (a safe box with an envelope could be enough, but if you can afford a digital vault, much better). Shared accounts are a nice gate inviting bad people trying to hack into our network.
What we can Achieve by Segregation of Duties
With several accounts for different roles on our environments will help us to protect from “Lateral Movement Attacks”. Once one identity is in compromise, the attacker will try to use it in several assets (the 500 computer example I provide earlier, the attacker will try the credentials on each of those, and it will try to harvest more credentials until being able to “elevate its rights”).
Each segregated asset and/or identity, will act as a security zone, or as a buffer zone that will help us to protect our assets. Assuming a hacker is trying to harvest credentials from non-privileged users:
- We have protection because Privileged accounts are segregated from non-privileged ones.
- We will have time to identify the attack and react before privileged accounts might be in compromise.
- We are able to find (and better audit) the segregated accounts.
In the worst-case scenario that a system gets compromised, this technic will help as a contention measure, just because the credentials of other environments are different.
Sadly, if our directory is the compromised one, then most likely the attacker might have access to all remaining systems. Bear in mind that Segregation Of Duties is just one brick in the wall… we need the rest!
